In the first part of the GlobaliD 101 series, we gave an overview of how our identity systems haven’t caught up to the modern world. We also provided suggestions of how digital identity should work.
The thing is, identity isn’t something your average person thinks about much. Typically, it’s a means to an end. If you want to take a trip to Europe, you need to bring your passport. Want to celebrate with a bottle of wine? You need to show your driver’s license.
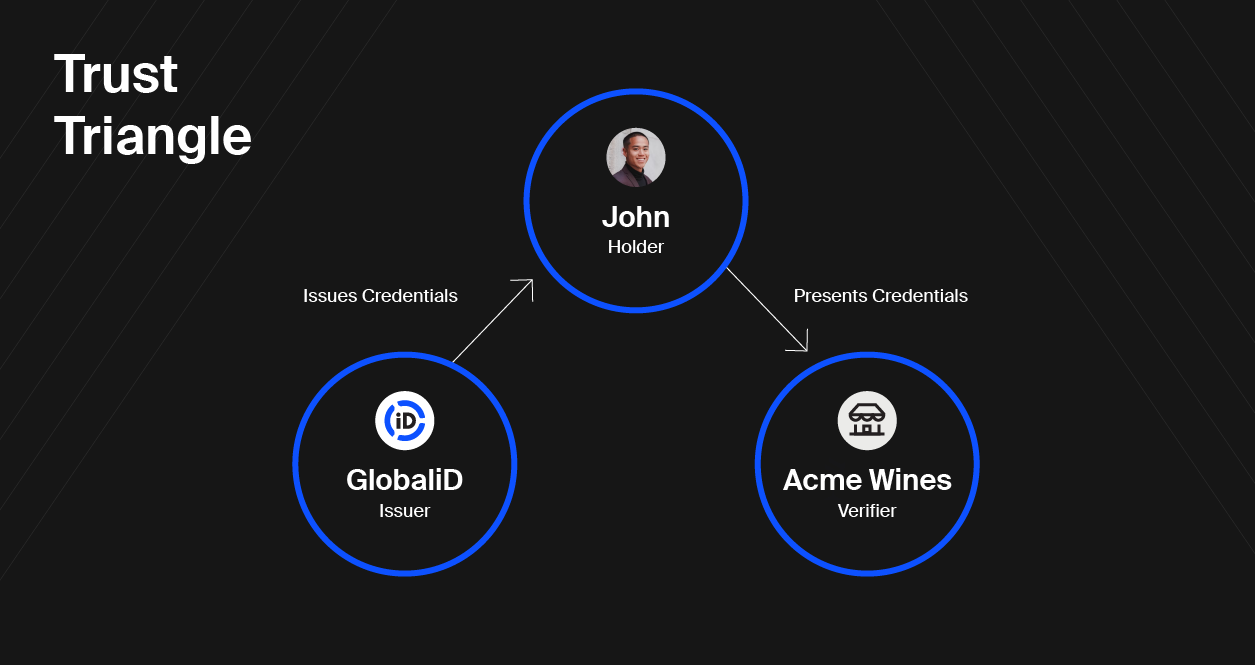
In part 2 of the GlobaliD 101 series, we’re going to explain how the process of identity actually works, and we’re going to do it with a really nifty concept we call the Trust Triangle.
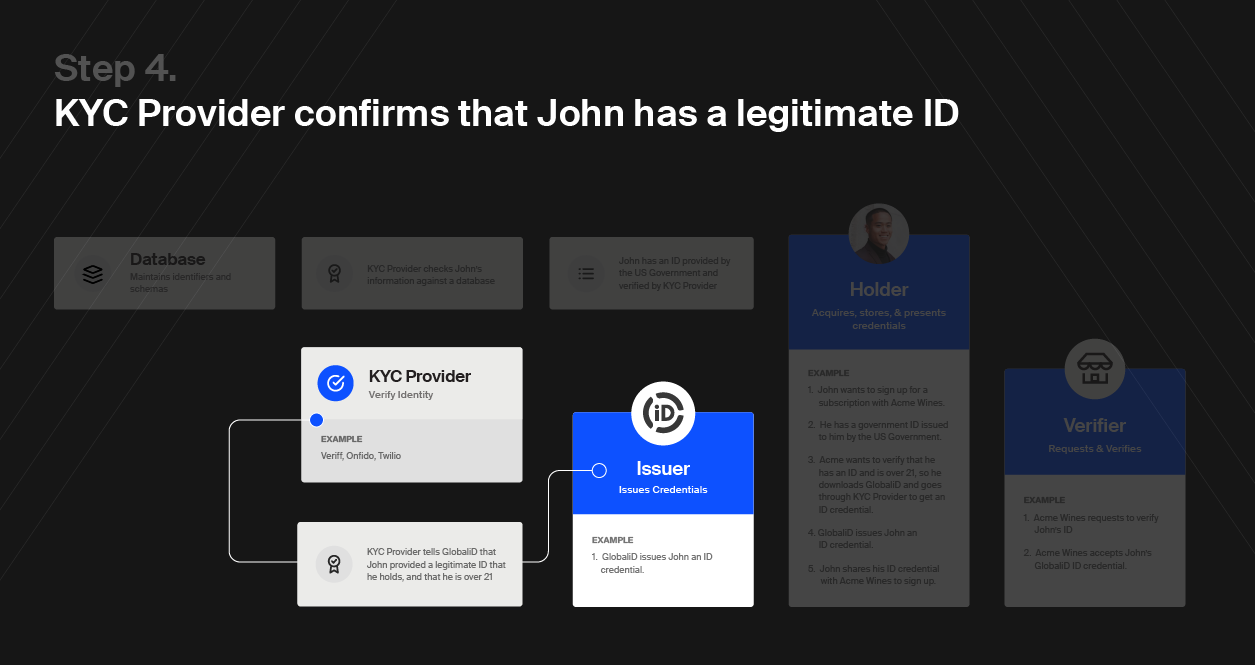
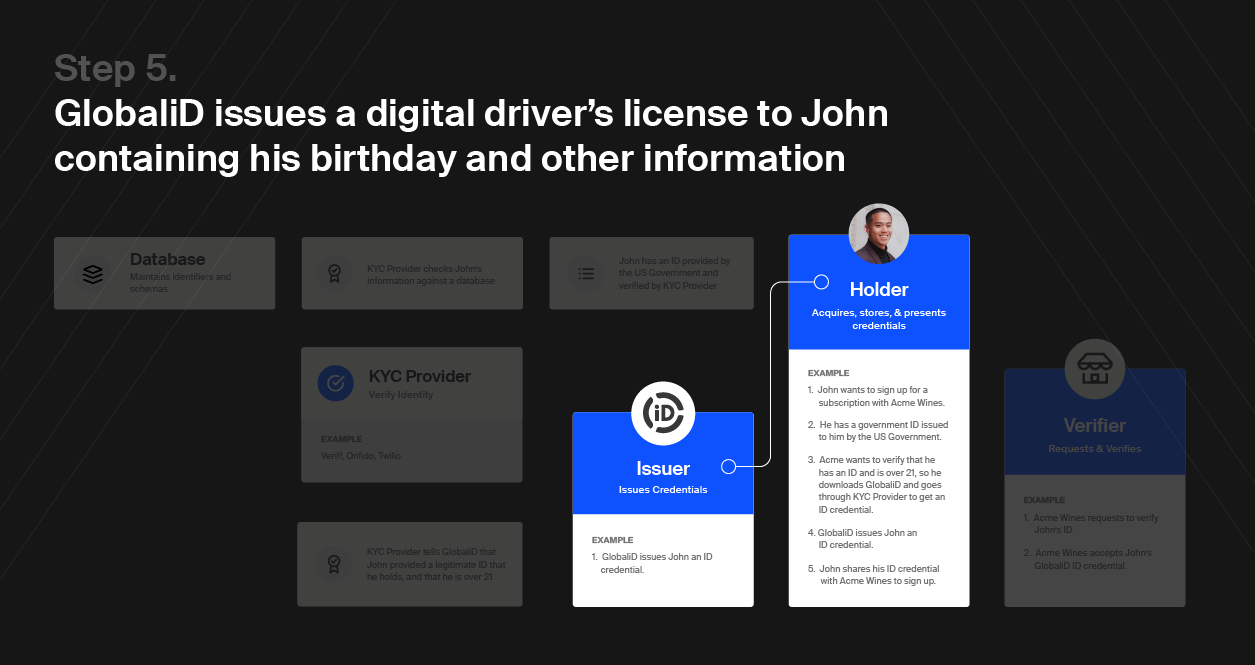
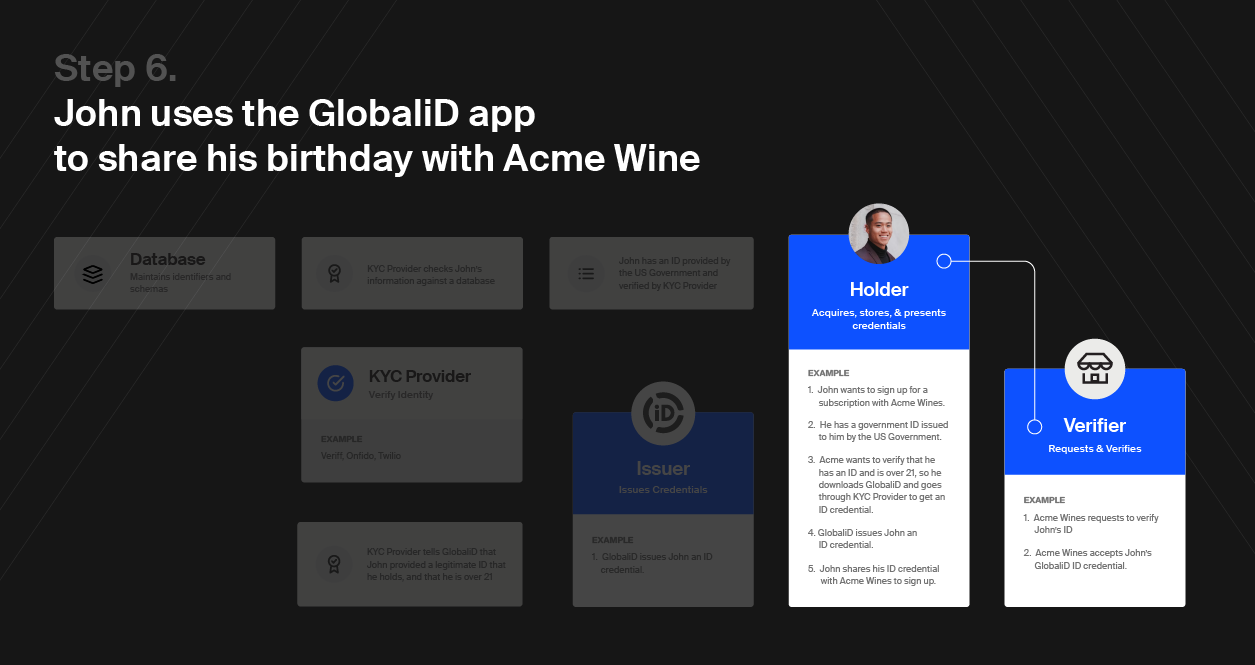
Here’s how the Trust Triangle works: Any identity framework is built on three pillars — issuers, holders, and verifiers. Together, these three pillars form the Trust Triangle.
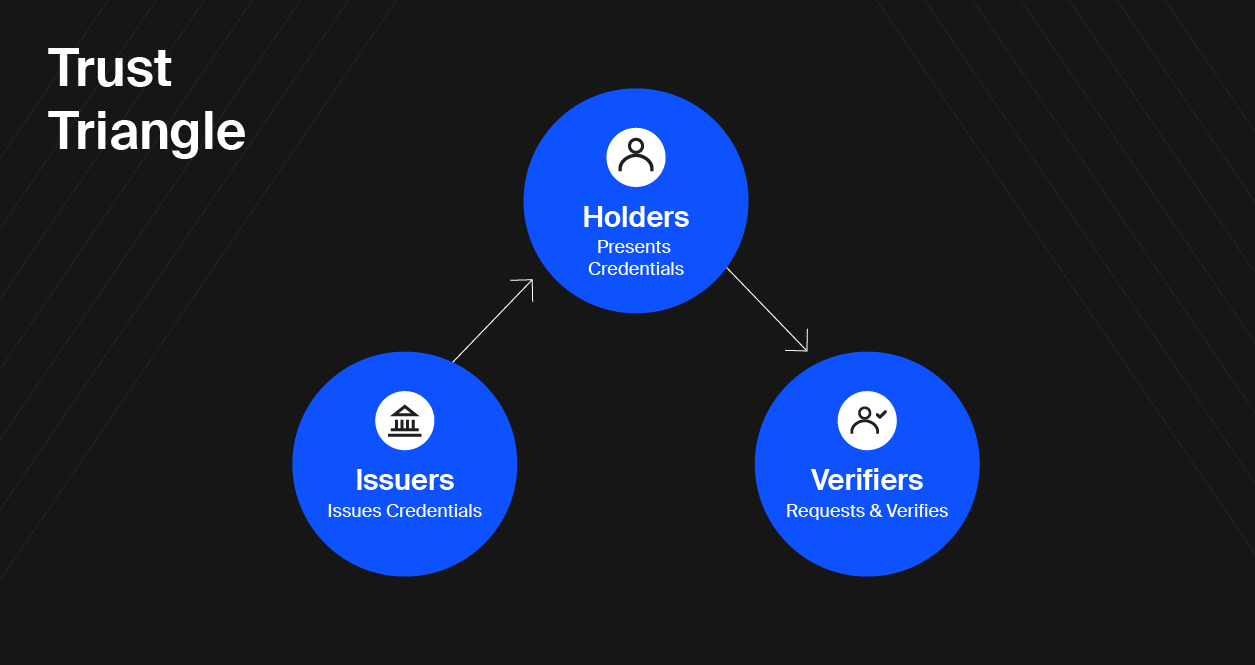
Consider a real life example: The Department of Motor Vehicles (DMV) issues you your driver’s license. You are now the holder of that credential. After your big promotion, you go to the store to pick up a moderately expensive bottle of wine. The store then verifies that you are of age by checking your license. Now, it’s time to celebrate.
Let’s break it down:
Issuers
Issuers are simply organizations that are authorized to issue credentials. They confirm that a piece of information is accurate and then issue a credential authenticating that information. They are typically trusted authorities who want to ensure compliance and enforce standards.
The Department of Motor Vehicles is an issuer. They issue a driver’s license credential that enables you to legally operate a car.
Holders
A holder is the owner of a credential. They can be individuals or organizations. They are trying to do something, but need some sort of credential to do it. They also need a place to store the credentials they already have and new ones they will acquire.
If you want to drive a car then you would go to the DMV (the issuer), and they would issue you a driver’s license credential which would enable you (the holder) to drive.
Verifiers
Verifiers are entities that receive a credential presented to them from a holder, confirm the credential comes from a trusted issuer, and then use that credential to perform a service or sell a good to the holder.
If a cop pulls you over while driving the first thing they are going to do is verify you are legally allowed to drive. To do this, the cop (the verifier) will ask you (the holder) to present your driver’s license credential that you received from the DMV (the issuer).
The Trust Triangle breaks down online
So far, everything has been pretty straightforward as this is how identity has always worked in the real world. But once we get online, things get a bit messy.
Consider the context of the Trust Triangle for a typical online transaction such as ordering food or drinks.
When ordering alcohol from a food delivery service such as Doordash, they will require you to upload a photo of your driver’s license in order to verify your age. Your ID is then kept and “stored securely by DoorDash for future alcohol purchases.”
The same problem occurs when booking a stay on the online marketplace Airbnb. In order to secure a place, hosts will often ask you to submit a photo of your government ID in order to verify you are who you claim to be.
This setup results in a slew of security and ownership. On the one hand, verifiers must now manage the security and privacy concerns of holding personal user information, which is now vulnerable to data breaches. On the other hand, individuals lose control of their identity once their identifying documentation is out in the wild.
In both scenarios, DoorDash and Airbnb hosts don’t need to hold your driver’s license. The former does it out of convenience (but with consequences). The latter does it because of the lack of a better alternative.
This breakdown of the Trust Triangle is taken to logical extremes in the context of Big Tech.
Consider how identity with Facebook works:
Facebook issues you an account, one of many fragmented identities we have online, after signing up with your email address. Facebook also holds all of your social data and personal information (username, password, first and last name, email, etc.) on their own servers. Facebook verifies your identity by confirming that you know your username and password, thus granting you temporary access to your social identity when you log onto their platform.
Something about this relationship feels a little lopsided!
The reality is that many of our online identity systems represent a complete breakdown of the Trust Triangle. What we need is a more empowering approach that preserves individual ownership of our digital identities.
Restoring the Trust Triangle in a digital world
The Trust Triangle is all about balance. Unfortunately, that balance skewed away from individuals when we transitioned to a digital reality.
At GlobaliD, we believe that people should own and control their digital identities. In the context of the Trust Triangle, it means that individuals should be holders of their identity and their credentials.
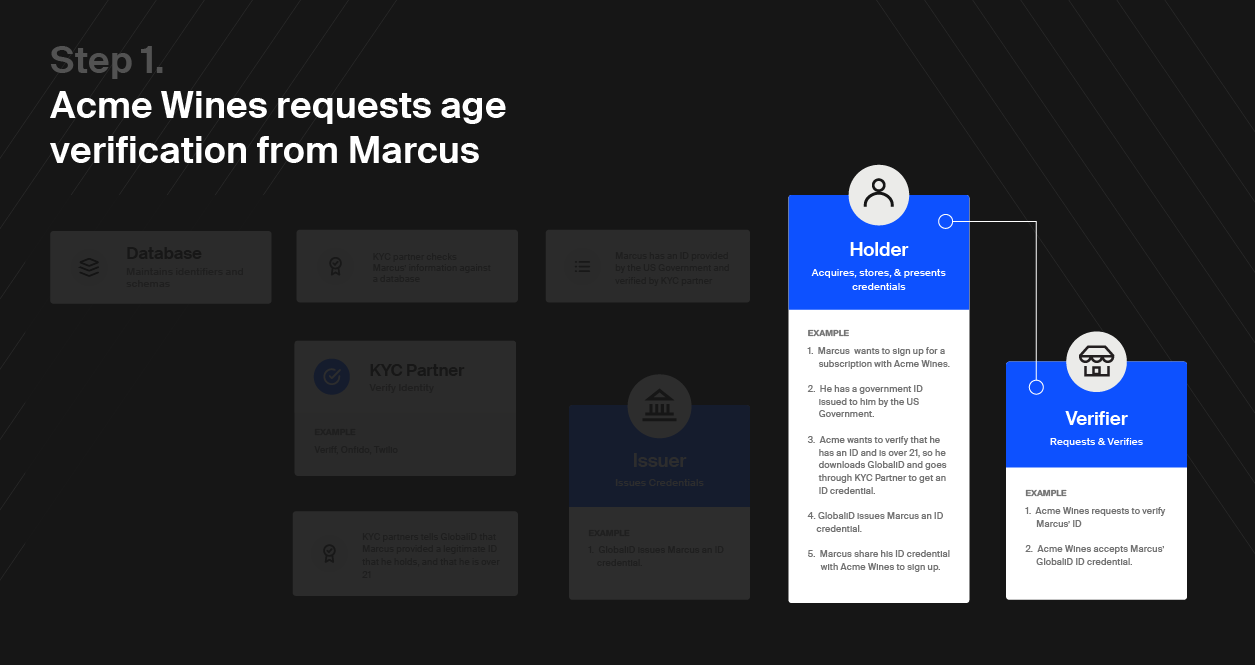
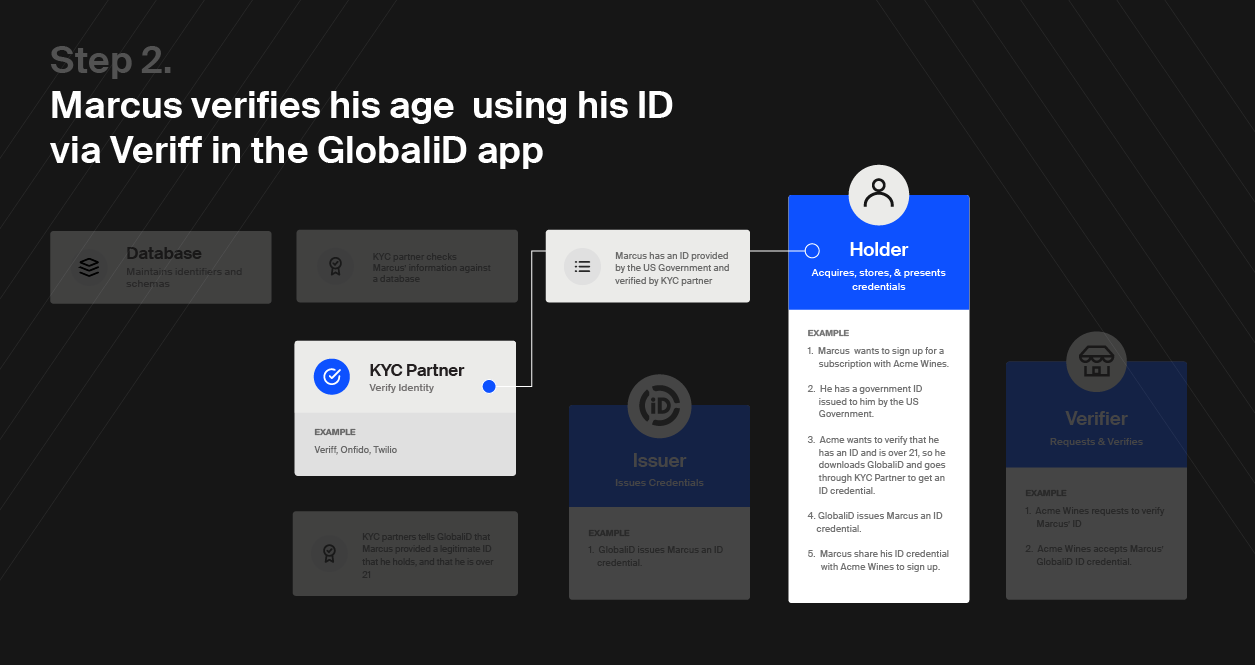
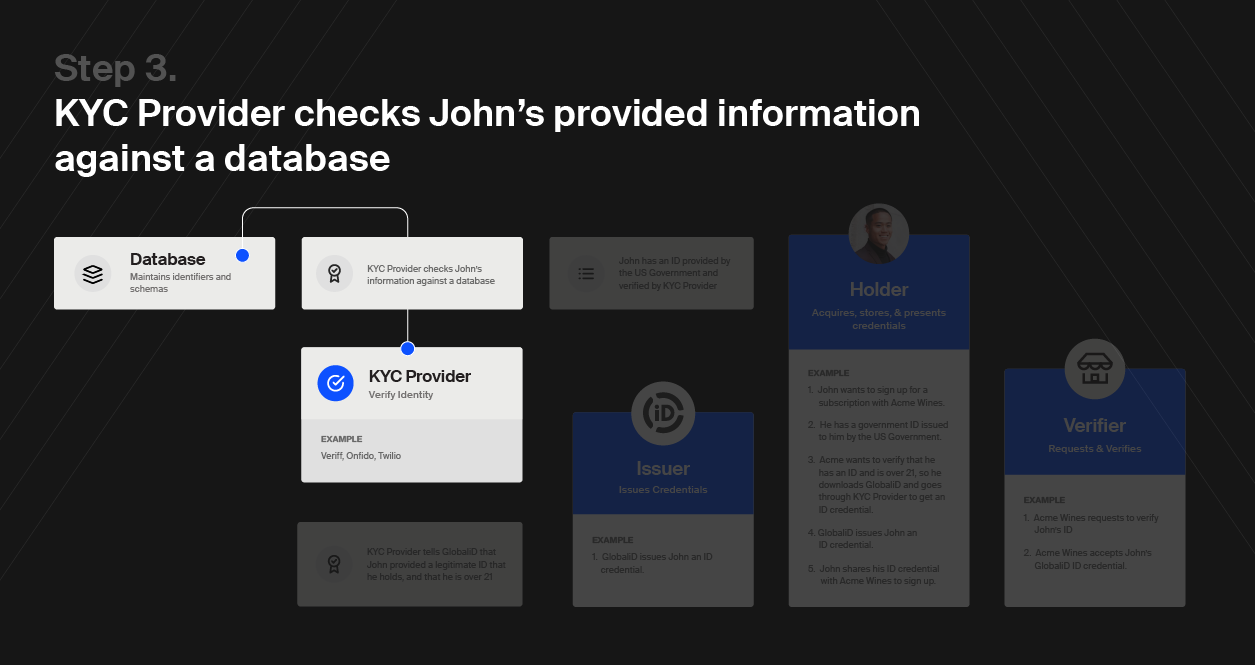
So how do we restore balance to the Trust Triangle in the digital world? Here’s how GlobaliD works in the context of the Trust Triangle: